In this post I mentioned about getting an A+ rating on ssllabs.com. It was not easy for me to get an A+ on some of the other sites like HT Bridge, but I finally got it! And with it I got compliance with:
- PCI DSS
- HIPAA
- NIST
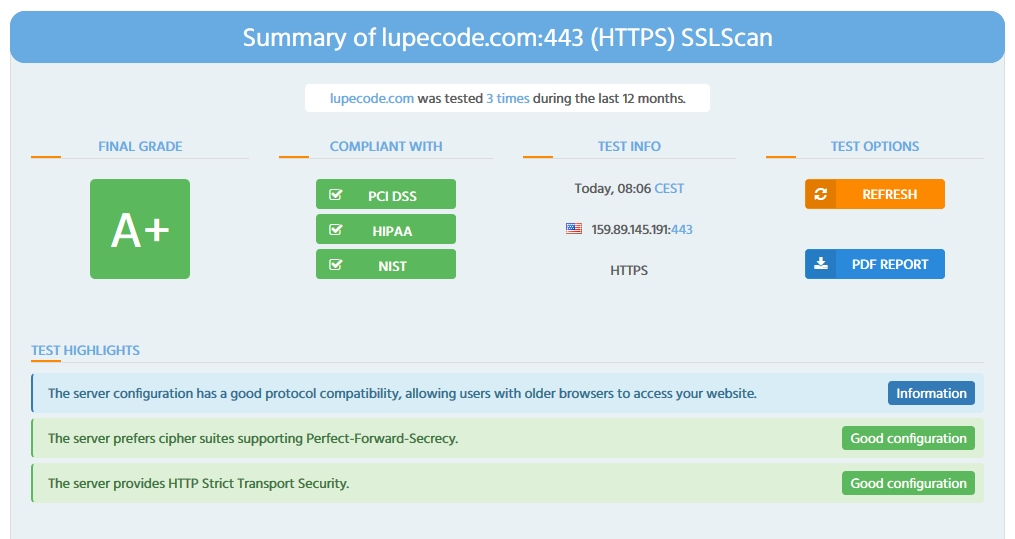
I’m impressed, and here is how I did it.
I’m still using Let’s Encrypt for my security certificates, but I’ve made a change to how I’m getting them. I’ve added the must-staple flag to certbot. I’m using DigitalOcean and their DNS with the CertBot DO DNS plugin, so my command looks like this:
|
1 |
certbot certonly --domain "$domain" --domain "*.$domain" --server "https://acme-v02.api.letsencrypt.org/directory" --dns-digitalocean --dns-digitalocean-credentials "/root/.secrets/certbot-digitalocean.ini" --must-staple --rsa-key-size 4096 |
To use this plugin you will need to get an API key from DO with write permission. I saved mine to /root/.secrets/certbot-digitalocean.ini, and it needs to be formatted like this:
|
1 |
dns_digitalocean_token = 012345789abcdef... |
In order to use it, I needed to make some changes to my /etc/letsencrypt/options-ssl-apache.conf and /etc/apache2/mods-available/ssl.conf files. This is what they look like now.
|
1 2 3 4 5 6 7 8 9 |
SSLEngine on SSLProtocol all -SSLv2 -SSLv3 -TLSv1 SSLCipherSuite ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:ECDHE-ECDSA-DES-CBC3-SHA:!DSS SSLHonorCipherOrder on SSLCompression off SSLSessionTickets off SSLOptions +StrictRequire LogFormat "%h %l %u %t \"%r\" %>s %b \"%{Referer}i\" \"%{User-agent}i\"" vhost_combined LogFormat "%v %h %l %u %t \"%r\" %>s %b" vhost_common |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
<IfModule mod_ssl.c> SSLRandomSeed startup builtin SSLRandomSeed startup file:/dev/urandom 512 SSLRandomSeed connect builtin SSLRandomSeed connect file:/dev/urandom 512 AddType application/x-x509-ca-cert .crt AddType application/x-pkcs7-crl .crl SSLPassPhraseDialog exec:/usr/share/apache2/ask-for-passphrase SSLSessionCache shmcb:${APACHE_RUN_DIR}/ssl_scache(512000) SSLSessionCacheTimeout 300 SSLUseStapling On SSLStaplingCache "shmcb:/logs/ssl_stapling(32768)" </IfModule> |
